SecurEnds Home
A Smart Approach To
Identity Governance & Administration
Simplify Access, Strengthen Compliance – Start with UAR, Scale to IGA
Human Identity
SecurEnds enables managers, entitlement owners, and application owners to conduct both single and hierarchical access reviews for employees, vendors, and contractors. Organizations can aggregate identity data from multiple applications into a unified system of record, leveraging fuzzy logic to intelligently associate usernames and credentials across different platforms. This ensures a comprehensive and accurate identity review process.
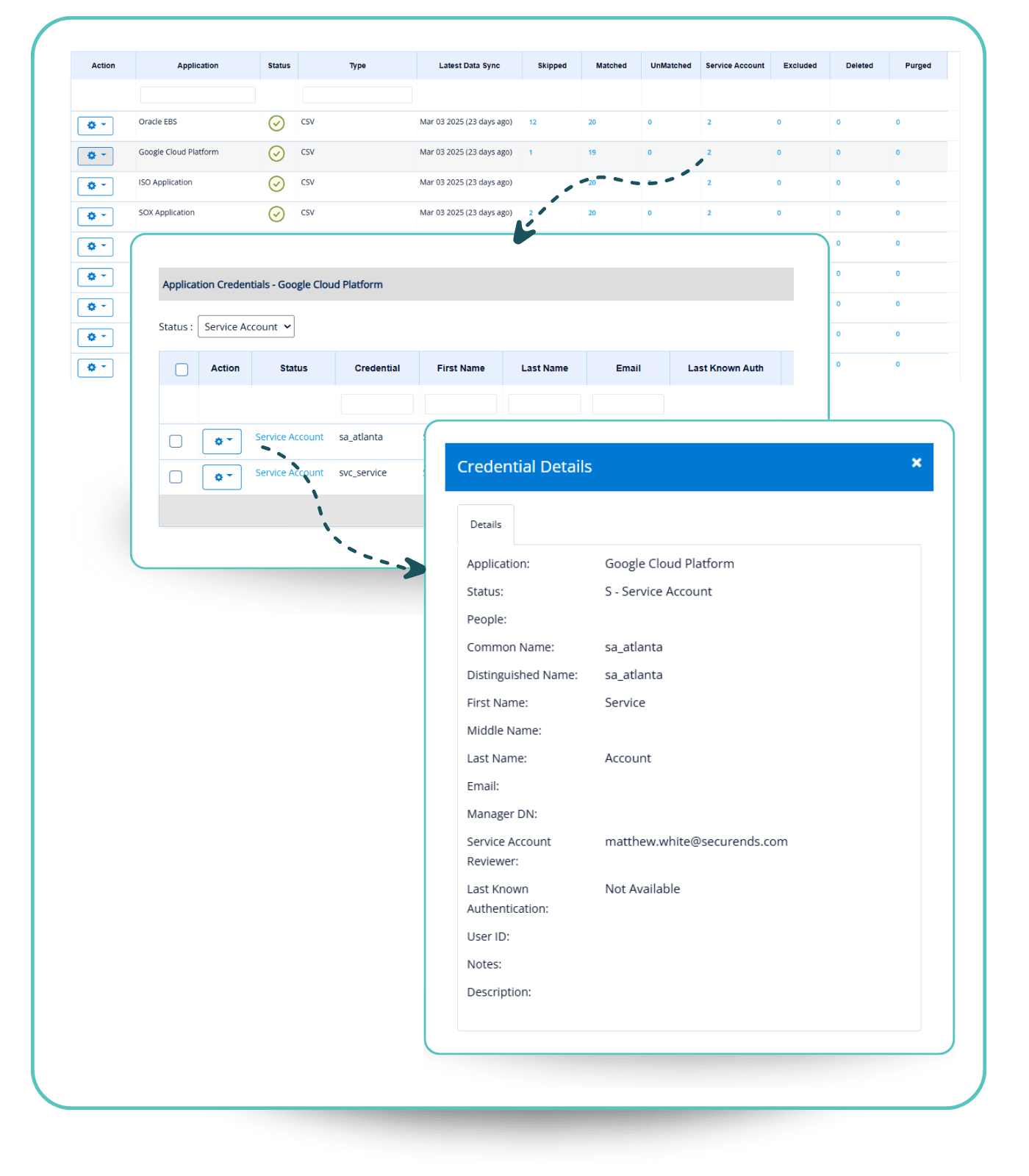
Non-Human Identity
SecurEnds Non-Human Identity Management streamlines the governance of service accounts, ensuring they are properly classified, reviewed, and assigned to responsible owners. Organizations can manually assign service accounts via the UI or use bulk assignment for efficiency. Service accounts are automatically included in access reviews, ensuring continuous monitoring and compliance.
Entitlement Management
SecurEnds enables entitlement management by continuously refining access policies, enforcing least-privilege principles, and eliminating security gaps. With SecurEnds, organizations can identify and remediate over-privileged users, orphaned accounts, and excessive entitlements, ensuring that future access requests align with business needs and security best practices. By dynamically adjusting entitlement policies, organizations can prevent privilege creep, reduce security risks, and maintain compliance with evolving regulatory requirements.
Connectors
SecurEnds provides extensive integration capabilities, ensuring seamless identity governance across diverse IT environments. The platform offers pre-built connectors for widely used applications, including directories, cloud services, HR systems, and collaboration tools, enabling rapid and efficient data ingestion.
For organizations with custom applications or niche systems, Flex Connectors allow integration through database queries, secure file transfers (SFTP), and API-based mappings. This ensures that identity data from virtually any source can be aggregated into a unified system of record.
Additionally, RPA-based connectors enhance automation by interacting with legacy systems that lack direct API access, bridging the gap between modern identity governance and older IT infrastructures.
By offering a combination of pre-built, flexible, and automation-driven connectors, SecurEnds empowers organizations to streamline access reviews, enforce governance policies, and improve overall security posture without operational complexity.
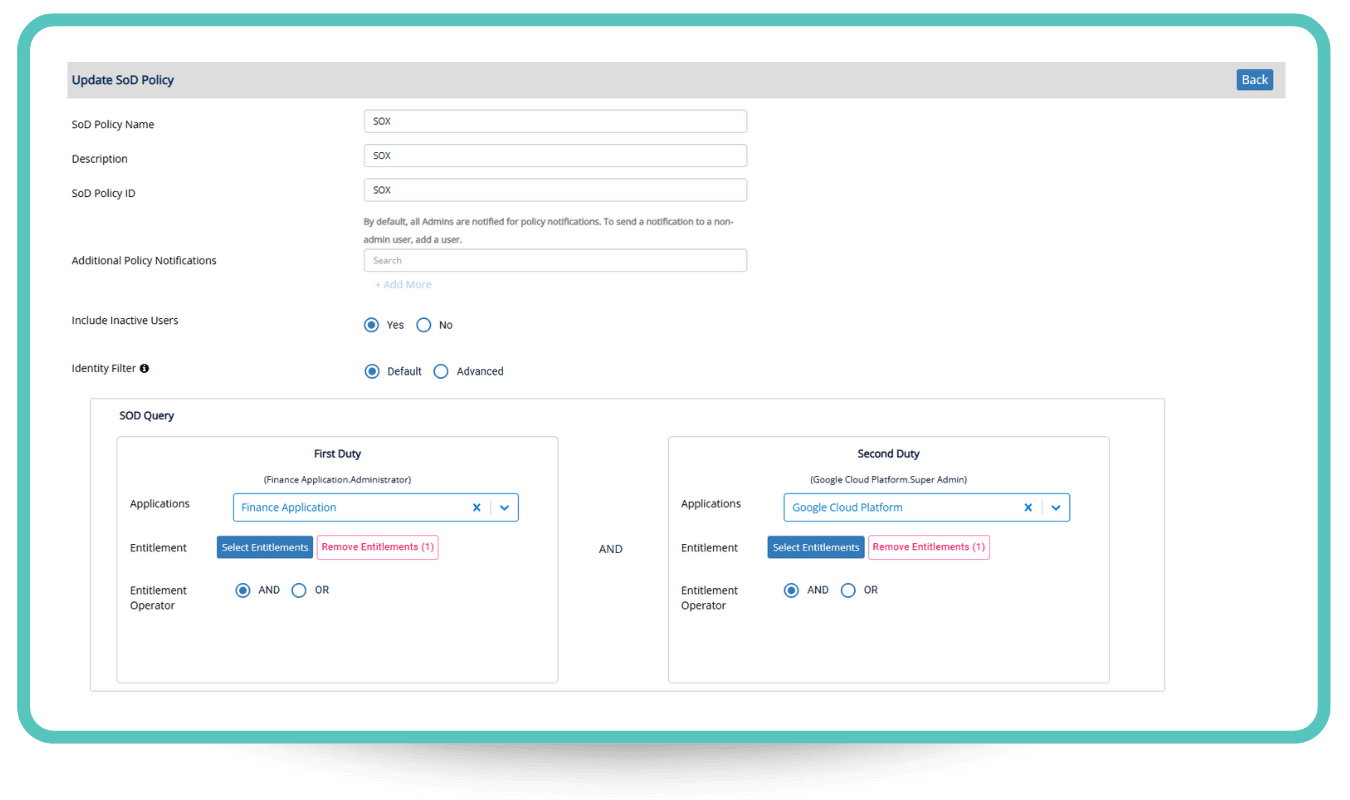
SoD Policy Builder
Ensure compliance and mitigate risk with SoD Policy Builder, enabling organizations to define and enforce Separation of Duties (SoD) policies across multiple applications. Administrators can create granular policies to prevent conflicts in access, such as restricting users from holding conflicting entitlements across different systems. With intuitive query-based configuration, organizations can easily enforce security best practices and reduce unauthorized access risks.
SoD Violation Reporting
Gain real-time visibility into policy violations with SoD Violation Reporting. This feature provides automated reporting on users who breach defined SoD policies, helping organizations quickly detect access conflicts that could lead to security threats. Reports can be scheduled daily, weekly, or monthly and exported in PDF format for audit and compliance tracking. Admins and designated recipients receive email notifications with detailed reports for proactive resolution.
Automated SoD Compliance Alerts
Stay ahead of security risks with Automated SoD Compliance Alerts. This feature ensures that administrators and designated stakeholders receive instant notifications whenever a policy violation occurs. The system automatically sends email alerts with attached reports, ensuring that violations are addressed promptly. By automating compliance monitoring, organizations can strengthen access governance and reduce the risk of fraud or insider threats.
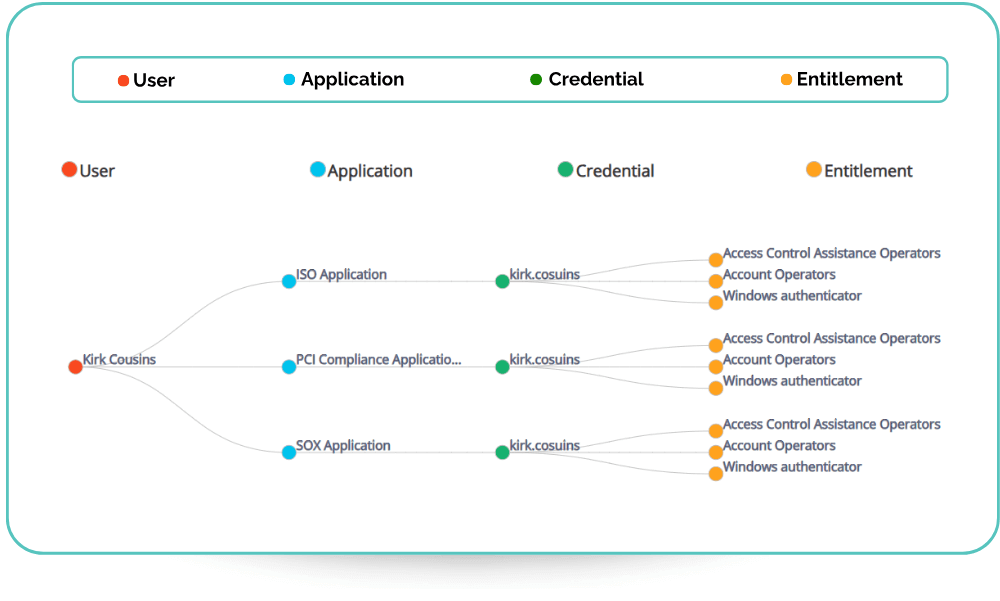
Identity MindMap
SecurEnds Identity MindMap Layout provides a user-centric view of access across applications and entitlements. It enables organizations to track a single user and identify orphaned accounts or access that exists outside the regular review cycle. This helps streamline deprovisioning, reduce security risks, and ensure only the necessary access is retained.
Application MindMap
SecurEnds Application MindMap Layout offers an application-centric perspective, displaying all associated users, credentials, and entitlements in a structured format. This view helps organizations identify and mitigate privilege creep, ensuring that users do not accumulate excessive access over time, thereby strengthening security and compliance efforts.
Entitlement MindMap
SecurEnds Entitlement MindMap Layout delivers an entitlement-centric view, mapping entitlements across applications and credentials. It is particularly useful for reviewing high-risk entitlements, such as administrative or privileged access, ensuring that critical permissions are properly assigned and regularly reviewed to prevent unauthorized access.
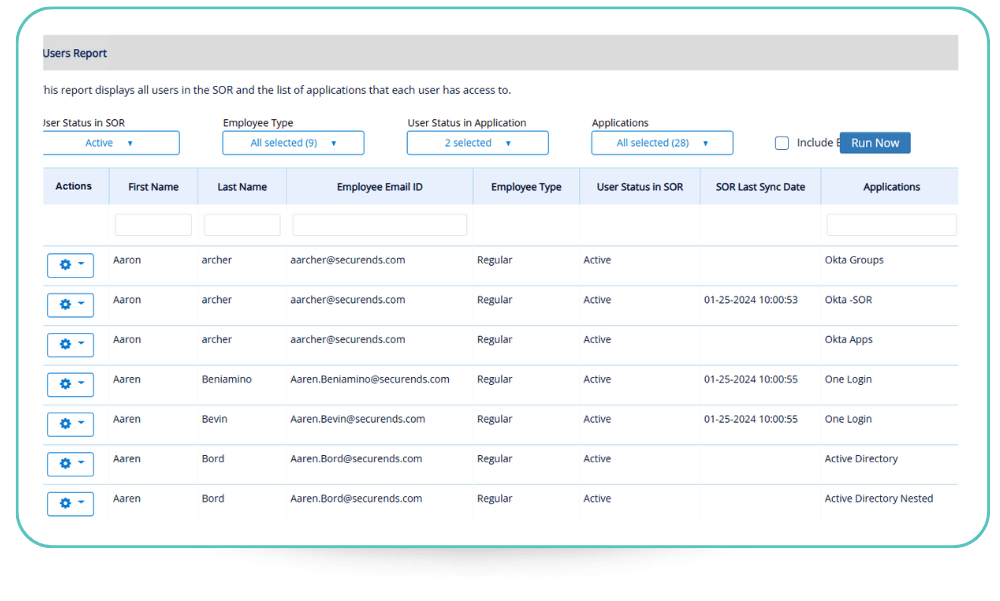
User Report
This is a powerful tool for license management, providing a complete view of all users in the System of Record (SOR) along with the applications they have access to. By exporting this data, organizations can track active licenses, identify unused or underutilized accounts, and optimize license allocation to reduce unnecessary costs. This report helps ensure that licenses are assigned efficiently, preventing over-provisioning while maintaining compliance with vendor agreements and internal policies.
Standard Self Service Access Request
SecurEnds Access Request Management streamlines the process of requesting and granting access across the organization. Users can select from three access types: Application Access, allowing direct requests for specific applications; Access Templates, enabling streamlined, role-based provisioning through pre-defined templates. Additionally, SecurEnds provides users with a centralized dashboard to track the progress of their access requests in real time allowing users to gain full transparency into the approval and fulfillment process, ensuring they stay informed at every stage.
Just-in-Time (JIT) Access
SecurEnds Just-in-Time (JIT) Access enhances security and compliance by granting users temporary, time-bound access to critical applications and resources only when needed. By eliminating standing privileges, JIT access reduces the attack surface, minimizes privilege creep, and enforces least privilege principles. Users can request access dynamically, ensuring that permissions are granted only for a defined duration before being automatically revoked.
Access Request Template
Templates simplify and standardize access provisioning by enforcing Role-Based Access Control (RBAC). Instead of handling access requests individually, organizations can leverage predefined templates to automate and streamline role-based access assignments. With Access Request Templates, users can request access based on their role rather than manually selecting individual permissions, ensuring consistent access provisioning across departments and reducing entitlement creep. This approach accelerates approval processes by aligning requests with predefined business roles and policies, minimizing security risks by eliminating ad-hoc or unnecessary access requests.
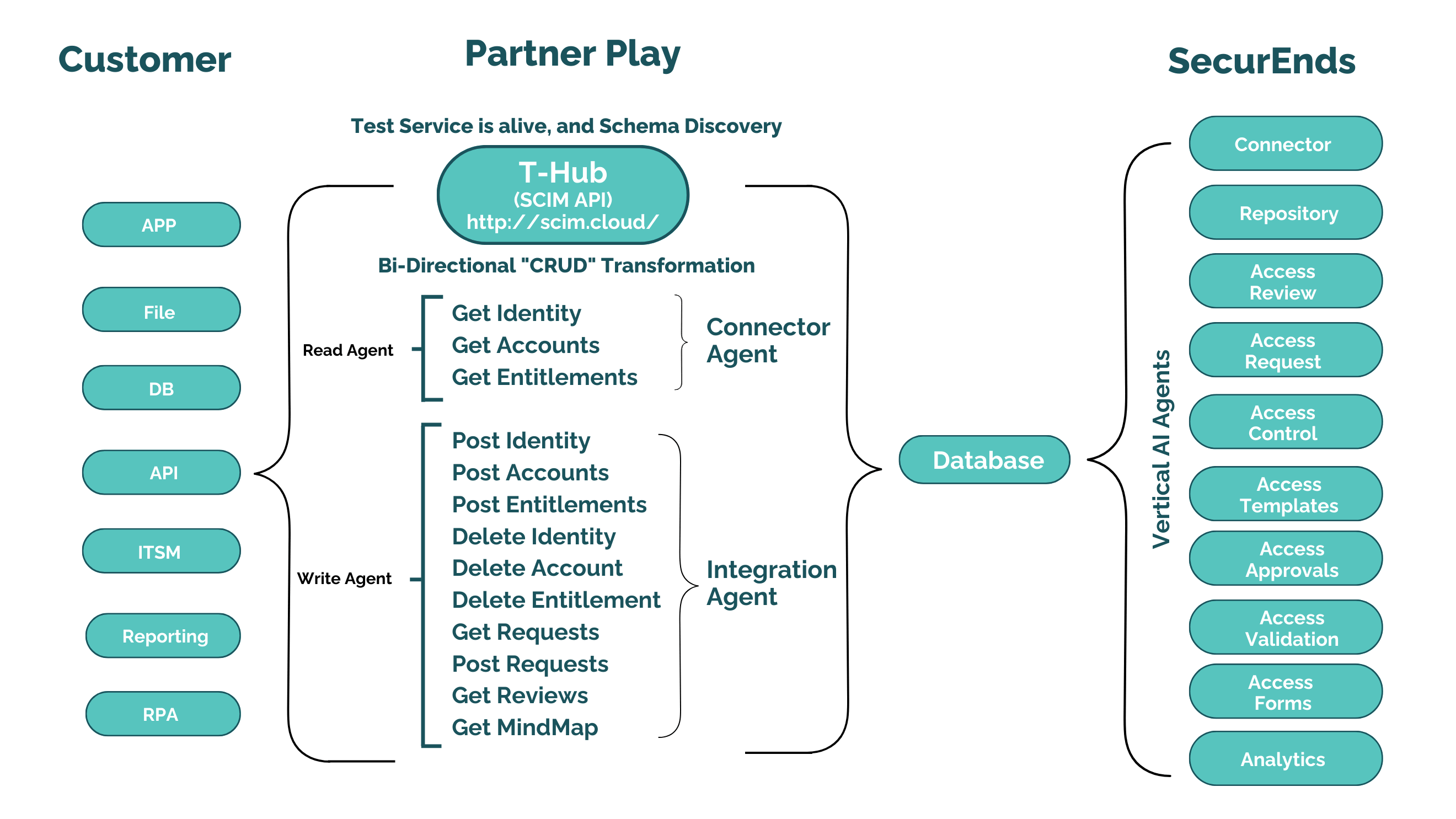
T-Hub – SCIM Access Provisioning and Deprovisioning
SecurEnds T-Hub simplifies user lifecycle management with SCIM (System for Cross-domain Identity Management) provisioning, enabling automated user provisioning, updates, and deprovisioning across multiple applications. By integrating with SCIM-supported systems, T-Hub ensures real-time identity synchronization, enforces role-based access control (RBAC), and minimizes unauthorized access, enhancing security and compliance
SecurEnds’ Way to IGA Success
Discover & Inventory Identities and Applications:
- Before you can manage access, you need a Governance Platform that gives you full visibility.
- Automatically inventory all applications, identities, entitlements, and accounts in a single platform.
- Gain real-time insights into “who has access to what” across your organization.
- Establish a centralized, policy-driven governance framework to eliminate shadow IT and redundant accounts.
Automate Access Reviews and Certifications:
- Manual access reviews lead to rubber-stamping and compliance gaps. We fix that.
- Replace spreadsheet-driven access audits with automated access review campaigns via Slack, Teams
- Set up single or multi hierarchical review campaigns for line managers, application owners, entitlement owners etc .
- Focus on non-human privileged accounts instead of wasting time on low-risk entitlements
Role-Based Access with Templates
- Custom access models lead to complexity. Standardizing access ensures security and efficiency.
- Define role-based access templates (e.g., Software Developer, Financial Analyst, QA Engineer).
- Pre-bundle access entitlements into easily requestable and reviewable templates.
- Reduce IT overhead by allowing users to request access in bulk, instead of line-by-line approvals.
Empower Users with Self-Service Access Requests
- Empower users while maintaining control
- Employees and managers can request access for themselves or their teams via an intuitive self-service portal
- Access requests can be scoped by job title, reporting structure, or department.
- Multi-level approval workflows ensure requests pass through the right approvers (Manager → App Owner → Entitlement Owner).
Streamline Provisioning and Deprovisioning
- Eliminate lingering access and reduce security risks.
- Automatically provision access for new hires and revoke access when employees leave or change roles.
- Set time-bound and just-in-time access controls to remove unnecessary long-term entitlements.
- Replace outdated, pre-built connectors with an T-Hub, SecurEnds’ SCIM interface
HEAR FROM OUR CUSTOMERS
SecurEnds currently empowers more than 100 of the world’s most forward-thinking companies to fully automate user access reviews, entitlement audits, and access certification.
“SecurEnds has been a great tool to help me with my annual audits. I used to have to do everything manually with Excel spreadsheets and emails. Now I can upload all my data, create a campaign and send everything out with the click of a button. This has saved me countless hours and I love how SecurEnds continues to streamline processes and make things even easier for its users.”

“Works across cloud, mobile and legacy, thick-client applications enabling control of user identity. It was configured to auto-launch and authenticate the user with frequently used applications on start-up and we have the ability to lock down access to systems by IP address providing assurance that data is protected.”
Senior Qa Automation Engineer

“we had problems to protect our access, its very important to manage and protect your credentials. my collage told me about this product and i am very satisfied its very easy to use and very flexible. today this product is part of my everyday life.””
Network Administrator

“Identity Access Management & Entitlement Reviews made easy! Compared to other enterprise solutions available in the market that has too many features that are rarely used but come with the hefty price tag this one is pretty good in what is provides at the cost and does the job!”
Nitin M., Product Management & Strategy, Financial Services (10,001+ employees)

“We are finally able to meet our Internal Audit and External Audit objectives for conducting Credential and Entitlement reviews.”
Steve M., Sr. Mgr Security & Compliance, Airlines/Aviation (1001-5000 employees)

“We were able to clearly define and manage Employee Onboarding, Lateral move, and offboarding. The tool can provide a lot of value for companies of reasonable size and pay for itself in months. “
Sreeram R., CTO, Information Technology and Services (11-50 employees)

WHO WE EMPOWER
Compliance & Audit Manager
Role: Ensures that the organization meets regulatory requirements and passes security audits.
Challenges: Lack of centralized tracking for user access reviews and approvals
Struggles with proving proof of compliance to auditors Manual processes that slow down audit responses
SecurEnds Solution:
Automates User Access Reviews (UARs) with Delta Campaigns, reducing redundant reviews.
Provides detailed audit trails and access review reports for SOX, HIPAA, and GDPR compliance
Identity & Access Management (IAM) Administrator
Role: Manages identity governance and access control.
Challenges: Manual user provisioning and deprovisioning delays operations.
Privilege creep due to weak entitlement enforcement. Difficulty maintaining audit readiness for SOX, HIPAA, and other regulations.
SecurEnds Solution:
Automates provisioning & deprovisioning with SCIM-based T-Hub.
Enforces RBAC using Access Request Templates for standardized access.
Security Analyst
Role: Analyzes and mitigates security threats related to user access and system vulnerabilities.
Challenges: Difficulty tracking unauthorized access and excessive privileges
Lack of a centralized system to monitor non-human identities (NHIs) Orphaned accounts and unrotated credentials creating security risks
SecurEnds Solution:
Automates risk-based access reviews to detect overprivileged users Tracks and governs service accounts, API keys, and AI agents with NHI Management Identifies unused credentials and orphaned accounts, triggering automatic remediation
IT Operations Manager
Role: Manages IT services, user access requests, and system performance.
Challenges: High volume of manual access requests leading to IT bottlenecks
Lack of an efficient way to track and approve access requests Difficulty keeping up with employee role changes and entitlement updates.
SecurEnds Solution:
Introduces Self-Service Access Requests, reducing IT workload Provides real-time tracking of access approvals through the My Requests dashboard
GET CONNECTED. STAY COMPLIANT.
Keep up with the latest industry news, receive SecurEnds product updates, follow our event schedule and learn how to reduce risk, easily provide proof of compliance and improve productivity.